Hashcat
is a newer tool that can utilize GPU power to crack nearly all types of
passwords. It supports multiple attacks like dictionary attacks and
brute force attacks to crack more than 200 different types of passwords.
Cracking with Hashcat is much faster than Aircrack-ng which we covered in our previous tutorial.
The tutorial will be covered in three steps.
- Capturing Handshakes with hcxdumptool.
- Converting Handshakes to Hashcat format.
- Cracking Handshakes.
Capturing Handshakes with hcxdumptool
Capturing Handshakes is the first step and most important step for cracking wifi password. Hcxdumptool provides another method to capture the handshakes and is the recommended method to capture packets by Hashcat developers which is another excellent password cracking tool.
Hcxdumptool is an easy and straightforward way to capture handshakes.
- You do not need to de authenticate the clients
- You can capture handshakes in bulk for all available networks which makes the whole process much simpler
Step-1 Install Hcxdumptool
By default, the tool does not come with Kali linux and you may need to install it. First of all update Kali Linux Repositories.
>sudo apt-get install hcxdumptool
Step-2 Check the Available Wifi Adapters.
Now check the wifi adapters available on your machine.
>iwconfig
>sudo systemctl stop NetworkManager
Step-3 Scan for Available Networks
Now scan for available networks.
>sudo hcxdumptool -i wlan0 --do_rcascan
Step-4 Capture traffic with hcxdumptool
Now to start the capture use the following command.
> sudo hcxdumptool -i wlan0 -o dumpfile.pcapng –active_beacon –enable_status=15
Here :
Converting Handshakes to Hashcat File format for cracking
In this part we are going to see, how we can convert the captured handshake to the fileformat that is recognizable by hashcat.
Step-1 Install Hcxtools
First of all we need to install the Hcxtools.
>sudo apt-get install hcxtools
Step-2 Convert the file
Now, to convert the file to the desired format, use the following command.
>hcxpcapngtool -o hash.hc22000 -E essidlist dumpfile.pcapng
Here
- hash.hc22000 is the converted file
- Essidlist will contain the list of SSIDs
- Dumpfile.pcapng is the source file
Now our file will be converted and stored in our home directory.
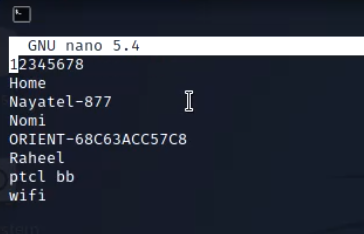
Step-3 Check ESSID lists
To check the essidlist file for name of wifi networks, use the following command.
>nano essidlist
Step-4 Check the mac address of target network
Now, we need the mac address of our target network, use the airodump tool again and copy the mac address.
>sudo hcxdumptool -i wlan0 --do_rcascan
Step-6 Delete excessive information from the converted file
Open the converted file and search for the target mac address. Just leave the information for the target and clear the rest of the file.
>nano hash.hc22000
Now, we have our converted file hash.hc22000. Just copy it from Vmware machine to your main Windows Machine where we will be actually cracking the password.
Step-7 (Optional) Convert handshakes captured though aircrack to Hashcat format
If you want to crack handshakes captured through aircrack tool with hashcat tool, use the following link to convert the handshakes from cap to hc22000 file format.
https://hashcat.net/cap2hashcat/
Now download the converted file and copy it to windows machine where we are actually going to crack the passwords.
Cracking Handshakes with Hashcat
Hashcat is a GPU based tool, so you need to have it running on a machine with a powerful graphics card with all drivers. It can be your windows machine, Ubuntu/ Kali machine or you can do it in the cloud.
Google, Azure and Linode are a few cloud service providers that offer GPU based VPS servers on rent. There is anther way to run hashcat on powerful cloud servers by running it through Jupyter-based notebooks(mostly used for machine learning)
- Google Collab
- Gradient
Cracking on cloud is very fast unless you have very fast GPU based machine. Now lets see, How we can crack passwords with Hashcat on Windows.
Step-1 Install Hashcat
Install the Hashcat from official website.
Step-2 Copy Handhashake to Hashcat folder
Step-3 Get the dictionary file
Step-4 Use Hashcat to crack the password
Open the Power shell in the hashcat folder and then use the command to crack the handshake
>.\Hashcat.exe -m 22000 -a 0 -o cracked.txt hash.hc22000 rockyou.txt
Here :
- 22000 tells the hashcat that its wifi password to be cracked
- Cracked.txt will store cracked passwords
- Hash.hc22000 is the source file
- Rockyou.txt is the dictionary file
Crack Passwords with Hashcat on Google Collab
- https://colab.research.google.com/github/mxrch/penglab/blob/master/penglab.ipynb
- https://colab.research.google.com/github/someshkar/colabcat/blob/master/colabcat.ipynb
- https://colab.research.google.com/github/ShutdownRepo/google-colab-hashcat/blob/main/google_colab_hashcat.ipynb
Install hashcat and required dictionaries while following instructions.Upload your hash file to an online file hosting provider like filebin.com or catbox.moe and then import it in your notebook with the following command in a new block
>!wget http://filebin.com/filenameCrack the handshake with following command
>!hashcat --status -m 22000 -a 0 -o cracked.txt hash.hc22000 /content/wordlists/rockyou.txt
Similarly you can use another service Gradient.run for running hashcat in the cloud.
Copy the code from collab notebooks to gradient notebooks and run it.